I posted about this about a decade ago but going through email this morning I found at least 8 or 9 questions from people in some way shape or form related to it so I figured I would re-post and maybe it will show up search engines more or perhaps people will realize it still works…
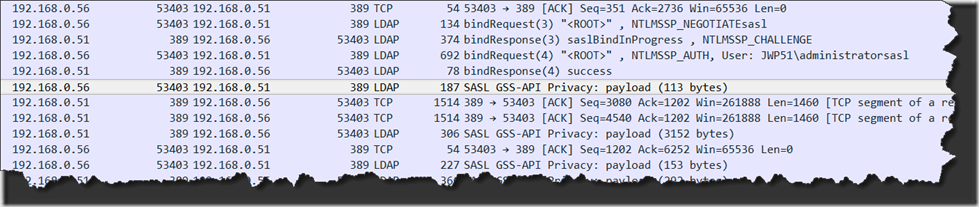
Q: Every time I look at a network trace from AdFind I see something like:
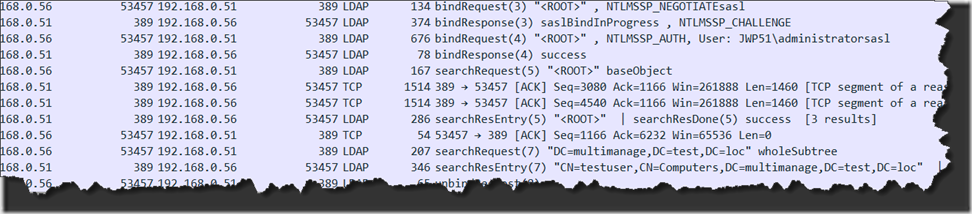
This is called LDAP Sealing. You can disable this by disabling Client Signing/Sealing. Once disabled the traffic should look like:
The current Client Signing setting is maintained in the registry (of course) in the key
HKLM\System\CurrentControlSet\Services\LDAP under the value LDAPClientIntegrity.
There are three possible values
0
No signing/sealing
1
Negotiate signing/sealing
2
Require signing/sealing
You will likely see it set to 1 if it is set to anything. If it isn’t set, the default internally is 1 anyway… So if you switch this to 0, you will *generally* start seeing the LDAP traffic in the clear and it should work with most LDAP API based apps. If you are trying to do this for another app and it isn’t work then the issue could very well be that the application itself is forcing the information to be “encrypted” anyway like the AdFind -kerbenc switch does. At that point you have no choice but to use Insight for AD[1] which hooks the LDAP calls prior to being encoded.
You can see the current value of the setting with:
reg query HKLM\System\CurrentControlSet\Services\LDAP /v LDAPClientIntegrity
You will see something like:
[Sat 07/07/2018 16:46:32.47]
E:\>reg query HKLM\System\CurrentControlSet\Services\LDAP /v LDAPClientIntegrity
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\LDAP
LDAPClientIntegrity REG_DWORD 0x1
If you want to quickly set it to 0 you can use the following command:
reg add HKLM\System\CurrentControlSet\Services\LDAP /v LDAPClientIntegrity /t REG_DWORD /d 0x00 /f
You will see something like:
[Sat 07/07/2018 16:46:43.63]
E:\>reg add HKLM\System\CurrentControlSet\Services\LDAP /v LDAPClientIntegrity /t REG_DWORD /d 0x00 /f
The operation completed successfully.
Note that this can also be set through Group Policy so you may find that you set it to 0 and then later it goes back to 1 or even possibly 2. If that happens a GPO was configured to define a value for Computer Configuration | Windows Settings | Security Settings | Local Policies | Security Options | Network Security: LDAP client signing requirements.
joe
[1] Insight for Active Directory (AD) is an old tool from SysInternals that used to absolutely rock. It hooked the LDAP API calls so every single call that came through you had visibility into what it was doing. At some point this tool broke hard and was worthless and was absolutely worthless for x64. However SysInternals eventually released a new version V1.2 which worked again but I personally have found it to be very hit and miss. Try it, if it helps you and you like it, awesome. Keep in mind that at least I have found this latest version to be quite sporadic on x64 Windows 10 missing calls as well as crashing outright. https://docs.microsoft.com/en-us/sysinternals/downloads/adinsight