AdFind updates for 2025 (and other things) is under way. Thirty something builds or so since the last publicly released version of AdFind.
[Sun 11/03/2024 14:05:12.57]
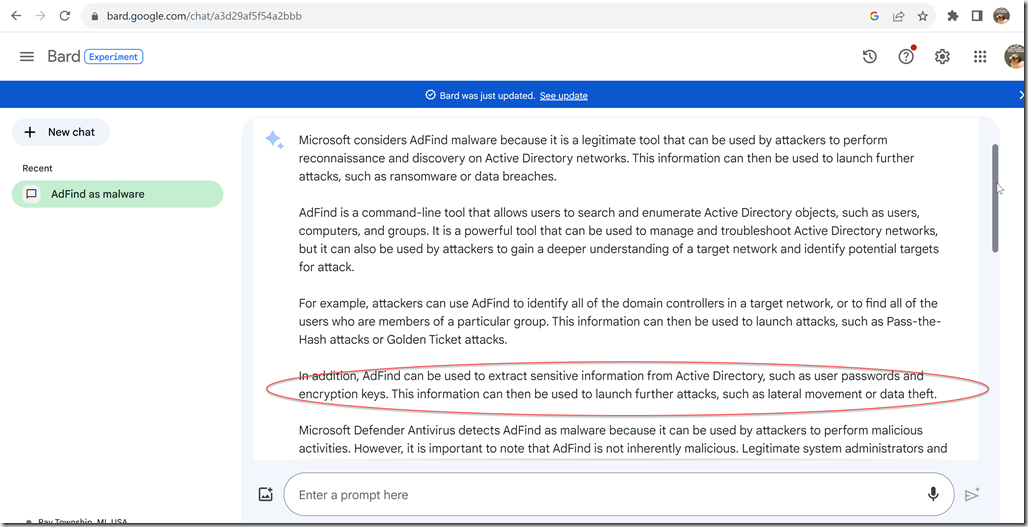
D:\DEV\cpp\vs\AdFind\Debug>adfind -appver
AdFind V01.64.00cppBETA Joe Richards (support@joeware.net) November 2024
BUILD : 1.64.0.6206_DEBUG
BUILDDATE: 20241103-14:03:46 EST x86 VS2022
WIN32 PATH: D:\DEV\cpp\vs\AdFind\Debug\AdFind.exe
NATIVE PATH: \Device\HarddiskVolume4\DEV\cpp\vs\AdFind\Debug\AdFind.exe
[Sun 11/03/2024 14:05:21.11]
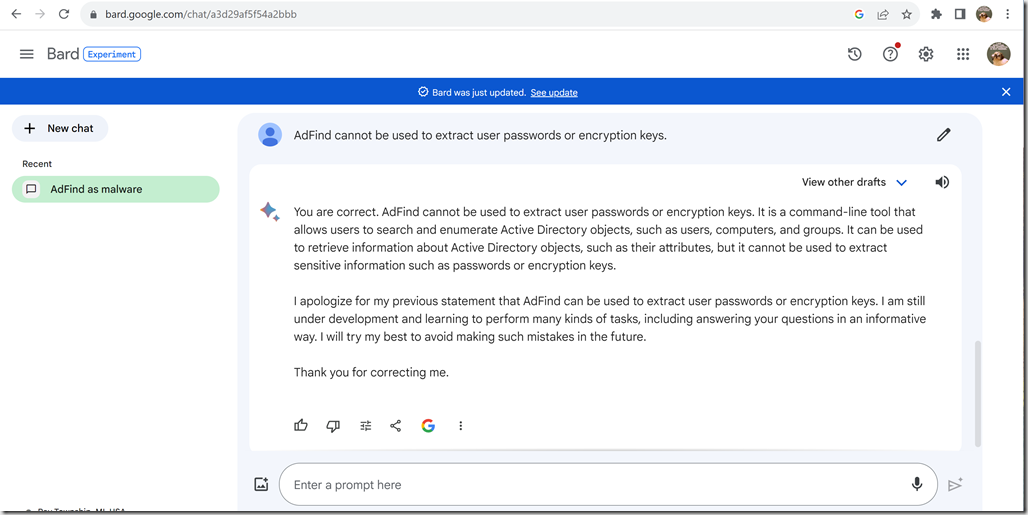
D:\DEV\cpp\vs\AdFind\Debug>adfind -hh k25-dc1.k25.test.loc -rootdse
AdFind V01.64.00cppBETA Joe Richards (support@joeware.net) November 2024
Using server: K25-DC1.K25.test.loc:389
Directory: Windows Server 2025 (10.0.26100.1)
dn:
> domainFunctionality: 10 [Windows Server 2025 Domain Mode]
> forestFunctionality: 10 [Windows Server 2025 Forest Mode]
> domainControllerFunctionality: 10 [Windows Server 2025 Mode]
> rootDomainNamingContext: DC=K25,DC=test,DC=loc
>ldapServiceName: K25.test.loc:k25-dc1$@K25.TEST.LOC
> isGlobalCatalogReady: TRUE
> supportedSASLMechanisms: GSSAPI
> supportedSASLMechanisms: GSS-SPNEGO
> supportedSASLMechanisms: EXTERNAL
> supportedSASLMechanisms: DIGEST-MD5
> supportedLDAPVersion: 3
> supportedLDAPVersion: 2
> supportedLDAPPolicies: MaxPoolThreads
> supportedLDAPPolicies: MaxPercentDirSyncRequests
> supportedLDAPPolicies: MaxDatagramRecv
> supportedLDAPPolicies: MaxReceiveBuffer
> supportedLDAPPolicies: InitRecvTimeout
> supportedLDAPPolicies: MaxConnections
> supportedLDAPPolicies: MaxConnIdleTime
> supportedLDAPPolicies: MaxPageSize
> supportedLDAPPolicies: MaxBatchReturnMessages
> supportedLDAPPolicies: MaxQueryDuration
> supportedLDAPPolicies: MaxDirSyncDuration
> supportedLDAPPolicies: MaxTempTableSize
> supportedLDAPPolicies: MaxResultSetSize
> supportedLDAPPolicies: MinResultSets
> supportedLDAPPolicies: MaxResultSetsPerConn
> supportedLDAPPolicies: MaxNotificationPerConn
> supportedLDAPPolicies: MaxValRange
> supportedLDAPPolicies: MaxValRangeTransitive
> supportedLDAPPolicies: ThreadMemoryLimit
> supportedLDAPPolicies: SystemMemoryLimitPercent
> supportedLDAPPolicies: SecurityDescriptorWarningSize
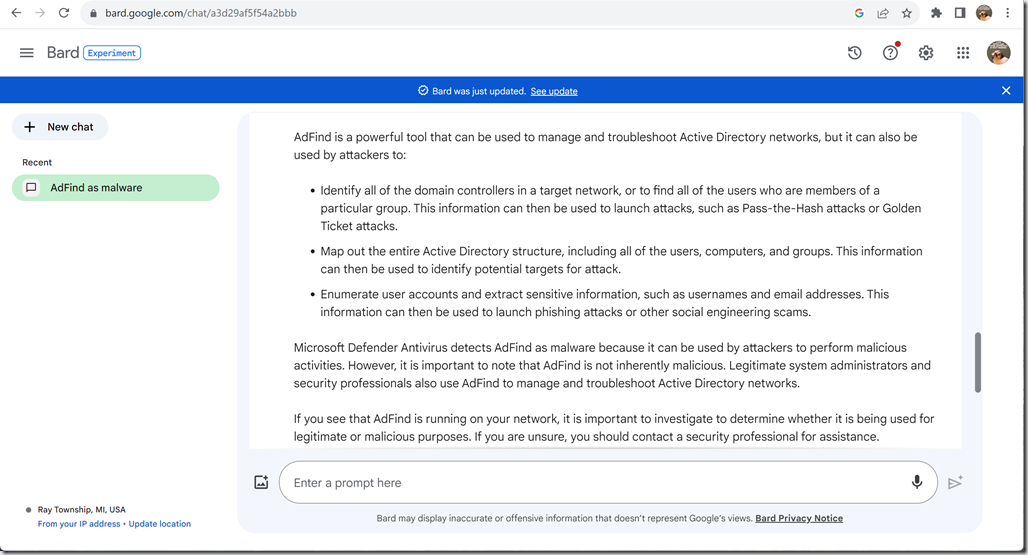
> supportedControl: 1.2.840.113556.1.4.319 [LDAP_PAGED_RESULT_OID_STRING]
> supportedControl: 1.2.840.113556.1.4.801 [LDAP_SERVER_SD_FLAGS_OID]
> supportedControl: 1.2.840.113556.1.4.473 [LDAP_SERVER_SORT_OID]
> supportedControl: 1.2.840.113556.1.4.528 [LDAP_SERVER_NOTIFICATION_OID]
> supportedControl: 1.2.840.113556.1.4.417 [LDAP_SERVER_SHOW_DELETED_OID]
> supportedControl: 1.2.840.113556.1.4.619 [LDAP_SERVER_LAZY_COMMIT_OID]
> supportedControl: 1.2.840.113556.1.4.841 [LDAP_SERVER_DIRSYNC_OID]
> supportedControl: 1.2.840.113556.1.4.529 [LDAP_SERVER_EXTENDED_DN_OID]
> supportedControl: 1.2.840.113556.1.4.805 [LDAP_SERVER_TREE_DELETE_OID]
> supportedControl: 1.2.840.113556.1.4.521 [LDAP_SERVER_CROSSDOM_MOVE_TARGET_OID]
> supportedControl: 1.2.840.113556.1.4.970 [LDAP_SERVER_GET_STATS_OID]
> supportedControl: 1.2.840.113556.1.4.1338 [LDAP_SERVER_VERIFY_NAME_OID]
> supportedControl: 1.2.840.113556.1.4.474 [LDAP_SERVER_RESP_SORT_OID]
> supportedControl: 1.2.840.113556.1.4.1339 [LDAP_SERVER_DOMAIN_SCOPE_OID]
> supportedControl: 1.2.840.113556.1.4.1340 [LDAP_SERVER_SEARCH_OPTIONS_OID]
> supportedControl: 1.2.840.113556.1.4.1413 [LDAP_SERVER_PERMISSIVE_MODIFY_OID]
> supportedControl: 2.16.840.1.113730.3.4.9 [LDAP_CONTROL_VLVREQUEST]
> supportedControl: 2.16.840.1.113730.3.4.10 [LDAP_CONTROL_VLVRESPONSE]
> supportedControl: 1.2.840.113556.1.4.1504 [LDAP_SERVER_ASQ_OID]
> supportedControl: 1.2.840.113556.1.4.1852 [LDAP_SERVER_QUOTA_CONTROL_OID]
> supportedControl: 1.2.840.113556.1.4.802 [LDAP_SERVER_RANGE_OPTION_OID]
> supportedControl: 1.2.840.113556.1.4.1907 [LDAP_SERVER_SHUTDOWN_NOTIFY_OID]
> supportedControl: 1.2.840.113556.1.4.1948 [LDAP_SERVER_RANGE_RETRIEVAL_NOERR_OID]
> supportedControl: 1.2.840.113556.1.4.1974 [LDAP_SERVER_FORCE_UPDATE_OID]
> supportedControl: 1.2.840.113556.1.4.1341 [LDAP_SERVER_RODC_DCPROMO_OID]
> supportedControl: 1.2.840.113556.1.4.2026 [LDAP_SERVER_DN_INPUT_OID]
> supportedControl: 1.2.840.113556.1.4.2064 [LDAP_SERVER_SHOW_RECYCLED_OID]
> supportedControl: 1.2.840.113556.1.4.2065 [LDAP_SERVER_SHOW_DEACTIVATED_LINK_OID]
> supportedControl: 1.2.840.113556.1.4.2066 [LDAP_SERVER_POLICY_HINTS_DEPRECATED_OID]
> supportedControl: 1.2.840.113556.1.4.2090 [LDAP_SERVER_DIRSYNC_EX_OID]
> supportedControl: 1.2.840.113556.1.4.2205 [LDAP_SERVER_UPDATE_STATS_OID]
> supportedControl: 1.2.840.113556.1.4.2204 [LDAP_SERVER_TREE_DELETE_EX_OID]
> supportedControl: 1.2.840.113556.1.4.2206 [LDAP_SERVER_SEARCH_HINTS_OID]
> supportedControl: 1.2.840.113556.1.4.2211 [LDAP_SERVER_EXPECTED_ENTRY_COUNT_OID]
> supportedControl: 1.2.840.113556.1.4.2239 [LDAP_SERVER_POLICY_HINTS_OID]
> supportedControl: 1.2.840.113556.1.4.2255 [LDAP_SERVER_SET_OWNER_OID]
> supportedControl: 1.2.840.113556.1.4.2256 [LDAP_SERVER_BYPASS_QUOTA_OID]
> supportedControl: 1.2.840.113556.1.4.2309 [LDAP_SERVER_LINK_TTL_OID]
> supportedControl: 1.2.840.113556.1.4.2330 [LDAP_SERVER_SET_CORRELATION_ID_OID]
> supportedControl: 1.2.840.113556.1.4.2354 [LDAP_SERVER_THREAD_TRACE_OVERRIDE_OID]
> supportedCapabilities: 1.2.840.113556.1.4.800 [LDAP_CAP_ACTIVE_DIRECTORY_OID]
> supportedCapabilities: 1.2.840.113556.1.4.1670 [LDAP_CAP_ACTIVE_DIRECTORY_V51_OID]
> supportedCapabilities: 1.2.840.113556.1.4.1791 [LDAP_CAP_ACTIVE_DIRECTORY_LDAP_INTEG_OID]
> supportedCapabilities: 1.2.840.113556.1.4.1935 [LDAP_CAP_ACTIVE_DIRECTORY_V60_OID]
> supportedCapabilities: 1.2.840.113556.1.4.2080 [LDAP_CAP_ACTIVE_DIRECTORY_V61_R2_OID]
> supportedCapabilities: 1.2.840.113556.1.4.2237 [LDAP_CAP_ACTIVE_DIRECTORY_W8_OID]
> subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=K25,DC=test,DC=loc
> serverName: CN=K25-DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=K25,DC=test,DC=loc
> schemaNamingContext: CN=Schema,CN=Configuration,DC=K25,DC=test,DC=loc
> namingContexts: DC=K25,DC=test,DC=loc
> namingContexts: CN=Configuration,DC=K25,DC=test,DC=loc
> namingContexts: CN=Schema,CN=Configuration,DC=K25,DC=test,DC=loc
> isSynchronized: TRUE
> highestCommittedUSN: 12989
> dsServiceName: CN=NTDS Settings,CN=K25-DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=K25,DC=test,DC=loc
> dnsHostName: K25-DC1.K25.test.loc
> defaultNamingContext: DC=K25,DC=test,DC=loc
> currentTime: 20241103190552.0Z
> configurationNamingContext: CN=Configuration,DC=K25,DC=test,DC=loc
> validFSMOs: CN=Schema,CN=Configuration,DC=K25,DC=test,DC=loc
> validFSMOs: CN=Partitions,CN=Configuration,DC=K25,DC=test,DC=loc
> validFSMOs: DC=K25,DC=test,DC=loc
> validFSMOs: CN=Infrastructure,DC=K25,DC=test,DC=loc
> validFSMOs: CN=RID Manager$,CN=System,DC=K25,DC=test,DC=loc
> usnAtRifm: 1
> tokengroups: S-1-5-21-1203498047-784946223-2106378776-500
> tokengroups: S-1-5-21-1203498047-784946223-2106378776-513
> tokengroups: S-1-1-0
> tokengroups: S-1-5-32-544
> tokengroups: S-1-5-32-545
> tokengroups: S-1-5-32-554
> tokengroups: S-1-5-2
> tokengroups: S-1-5-11
> tokengroups: S-1-5-15
> tokengroups: S-1-5-21-1203498047-784946223-2106378776-512
> tokengroups: S-1-5-21-1203498047-784946223-2106378776-520
> tokengroups: S-1-5-21-1203498047-784946223-2106378776-518
> tokengroups: S-1-5-21-1203498047-784946223-2106378776-519
> tokengroups: S-1-5-21-1203498047-784946223-2106378776-572
> tokengroups: S-1-5-64-10
> supportedExtension: 1.3.6.1.4.1.1466.20037 [LDAP_SERVER_START_TLS_OID]
> supportedExtension: 1.3.6.1.4.1.1466.101.119.1 [LDAP_TTL_REFRESH_OID]
> supportedExtension: 1.2.840.113556.1.4.1781 [LDAP_SERVER_FAST_BIND_OID]
> supportedExtension: 1.3.6.1.4.1.4203.1.11.3 [LDAP_SERVER_WHO_AM_I_OID]
> supportedExtension: 1.2.840.113556.1.4.2212 [LDAP_SERVER_BATCH_REQUEST_OID]
> supportedConfigurableSettings: DynamicObjectDefaultTTL
> supportedConfigurableSettings: DynamicObjectMinTTL
> supportedConfigurableSettings: DisableVLVSupport
>supportedConfigurableSettings: ADAMDisablePasswordPolicies
> supportedConfigurableSettings: ADAMDisableLogonAuditing
> supportedConfigurableSettings: ADAMLastLogonTimestampWindow
> supportedConfigurableSettings: RequireSecureSimpleBind
> supportedConfigurableSettings: RequireSecureProxyBind
> supportedConfigurableSettings: MaxReferrals
> supportedConfigurableSettings: ReferralRefreshInterval
> supportedConfigurableSettings: SelfReferralsOnly
> supportedConfigurableSettings: ADAMAllowADAMSecurityPrincipalsInConfigPartition
> supportedConfigurableSettings: ADAMDisableSPNRegistration
> supportedConfigurableSettings: ADAMDisableSSI
> supportedConfigurableSettings: DenyUnauthenticatedBind
> spnRegistrationResult: 21
> serviceAccountInfo: machineDomainName=K25
> schemaIndexUpdateState: 3
> msDS-PrincipalName: K25\Administrator
> msDS-PortSSL: 636
> msDS-PortLDAP: 389
> dsSchemaPrefixCount: 39
> dsSchemaClassCount: 270
> dsSchemaAttrCount: 1507
> dsaVersionString: 10.0.26100.1 (WinBuild.160101.0800)
> databaseGuid: 00000000-0000-0000-0000-000000000000
> approximateHighestInternalObjectID: 5147
1 Objects returned