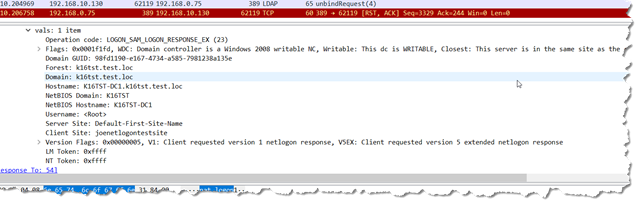
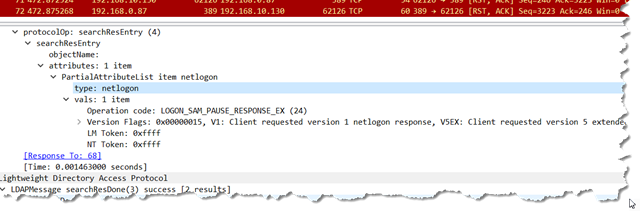
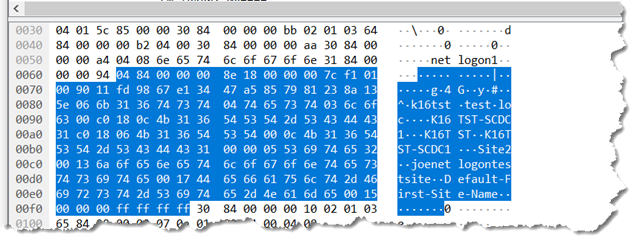
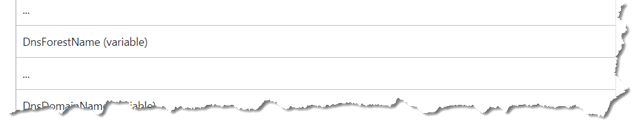
I have had quite a few people ask me to get to the getting and get the jwDCLocator.pl script made available for them to start looking at it.
So to help those folks out, I am going to do a “quick release” from the Blog and follow up with a release more similar to how I usually release tools on the main website.
You can now find the perl script in a 7zip archive at
https://www.joeware.net/downloads/sharedsource
Note: I have provided a link to the folder itself and enabled indexing so that people can see the whole folder and not think there is something else hidden in there where they can get source code to the other tools, which with the exception of rdp-sec-check (another perl script), is 100% absolutely positively NOT available[1]. I don’t provide source code for the stuff writtin in c/c++, don’t bother asking. I might change my mind in the future but it will be me changing my mind, not someone coercing or convincing me to change my mind.
As of right now, take a look at the usage in the script
jwDCLocator.pl /?
Or look at the code itself. You can run with an INI config file or with command line options. The simplest examples of running the script are
perl jwdclocator.pl /domain:k16tst.test.loc
and
perl jwdclocator.pl /domain:k16tst.test.loc /gclist
I have tested on CentOS7 and FreeBSD12 as well as Windows Server 2012 R2, Windows 10 1809, Windows Server 2016, and Windows Server 2019. For Windows Server both full and core.
For CentOS7 and FreeBSD12 I had to upgrade from perl V5.14 to perl 5.26 (or newer). There is some hashing functionality in the initial script that needs the alias/reference stuff in 5.26. Stuff that was apparently there before in older versions of perl that I swear I had used back in the 90’s for some monitoring scripts (I need to go look closer at those old scripts) but it seemed to have been lost along the way. I also needed to install Net::DNS and Net::LDAP.
For Windows I had to install perl 5.26 (or newer – usually Strawberry 5.28). Same reason for versioning as mentioned above. I also had to install Net::LDAP, Net::DNS was already there.
Mini-FAQ:
Q: Hey dude, I am getting weird results…
A: Feel free to run with the /verbose and /debug switches and then send me a text capture (not image) of the run screen including the command and all files created if you want me to look at it. If you have modified the script, share with me exactly what you did. As per my normal joeware warranty, I will try to look at it when I can, I may or may not fix it.
Q: Hey joe, where you going with that gun in your hand?
A: Haha. Excellent, never heard that one before…
Q: When will you release this in other script languages?
A: Maybe never. If you want it in another language, feel free to do it and then you can send it to me and I may (or may not) put it in the 7zip file with the perl script. I have to look at the code and feel comfortable with it if I am going to share it on my site. You understand of course.
Q: Can I incorporate this intellectual property in my program?
A: ABSOLUTELY YES. You have unrestricted rights to use anything in this script in any code you write nor and forever.
That is the whole point behind WHY I spent nights working on this so that I could make it hopefully simple to read and understand so that people would use this knowledge and understanding and actually implement this functionality in their code. Please acknowledge me somewhere saying hey, this dude really helped us out to make our product better but even that isn’t a requirement. I JUST WANT THE CODE OUT THERE IN THE WILD RELATED TO ACTIVE DIRECTORY TO GET BETTER. I truly love this technology and think MSFT changed the world with it and I have had 20 years of salary directly related to it. I expect to have many more. And if people start writing code to properly use it, well my life and the lives of many friends and many tens of thousands of people I have never met get better. This will help, hopefully, to remove some stupid from the world.
Too many companies out there pretend to be AD integrated or AD compatible when what they really mean is that they simply have an LDAP interface. I’m sorry to burst your bubble, that doesn’t make you AD integrated or AD compatible. You have multiple bars there, you can do LDAP? Great, that means you can see AD, that doesn’t mean you are integrated or compatible. You need to be able to find domain controllers properly with actual redundancy/high availability, you need to understand multiple domains in a single forest, you need to understand Global Catalog versus Domain. If I ask you about redundancy and availability and your response is something like give me a VIP/Load Balancer to point at I will look at you in disdain. If you want to use AD and you want to use LDAP, in particular, to hit AD. Do it right because you aren’t doing anyone any favors otherwise. I am looking at you IBM and your WebSphere product line in particular (which I pointed out to your ridiculously priced internal consultants all the way back in 2001 sucked and how you could fix it when I was at Ford Motor and your consultants were trying to say AD was failing), I am looking at you VMware, I am looking at you Splunk, so many companies, so little time.
If you think wow, this was really helpful and will make our product or my code or my scripts or whatever better, please consider the donate button up in the corner. Or not. That is entirely up to you. It is just a form of recognition and a statement to the value you think this stuff brings you. I am not starving but I won’t snub my nose at financial forms of appreciation either. ![]()
That’s it for now. More later. I have a new script I am working on specifically for *nix machines now to help further the admins/support teams in that space.
joe
[1] Well I did share the source code to one small tool to Kevin Mitnick (yes that Kevin Mitnick – and you all thought I was boring…) a few years back. Hackers seem to love me. Sometimes I wonder if I wasted my life being on the good side of IT and Security instead of being on the shadier side. ![]()