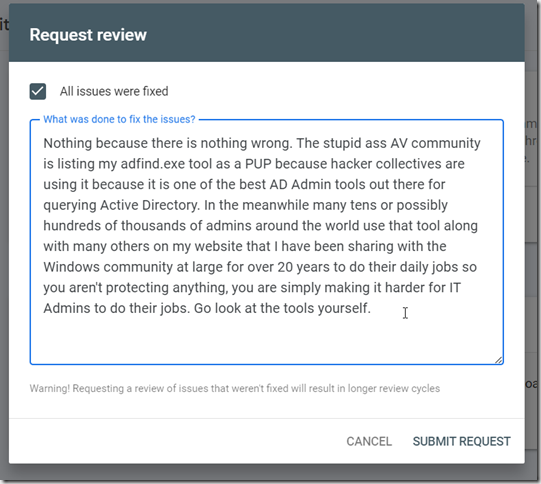
I am getting masses of emails about people having issues downloading from the site. Primarily AdFind is the one people are having issues with but Chrome has been blocking ALL downloads from the site.
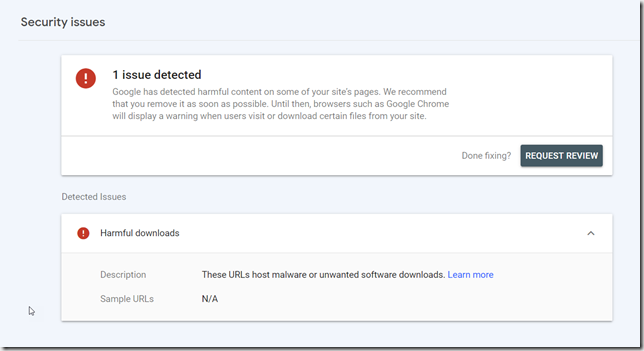
I have been trying to work with Google to get Chrome sorted out but they seem to be really confused over there in Googleland. They mark my site dangerous with no evidence of anything specific being wrong, I will then raise a request for review, they will then clear it and say it is fine but then I still can’t download. The next time I go look, they are saying the site is dangerous again, so I request review and they clear it again, over and over again. In the meanwhile you can turn off Safe Browsing in the settings to download the tools. I don’t really recommend running that way normally, but you can easily turn it on and off when you go to download the tools.
Brave is allowing downloads of everything but AdFind by default. AdFind can be downloaded if you go into the settings and select No Protection under Safe Browsing. Again, I do not recommend running that way normally but if you need to use it to download AdFind, this is the way. Just turn safe browsing back on afterwards.
FireFox, like Chrome, is alerting on all downloads, however you can easily bypass that while downloading by selecting Allow Download under download details.
Opera has zero issues downloading things.
Microsoft Edge will also download it but Defender may pop up and say it is killing it, you can tell Defender to go stand in the corner and ignore it. In fact you will need to do this regardless of which browser you use to download it because Defender will try to kill it.
Obviously, besides the browsers if you have antivirus or anti-malware software that could be attacking AdFind as well. You will need to tell that software to back off as well, likely if you are using this at work you will have to have your End Point Security people call off the dogs.
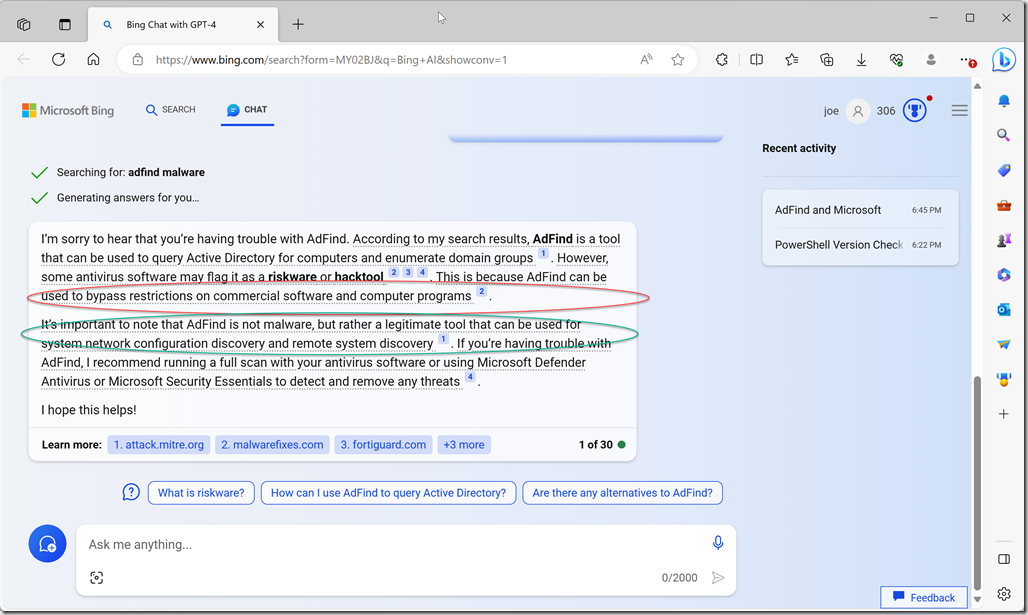
For any End Point Security people reading this, the Anti-virus/malware software vendors suck[1]. Instead of looking for specific questionable actions, they just slap labels on binaries and say “bad”. The reason AdFind is being labeled as “bad” is because hacker collectives have been using it to do recon work against AD because it is one of the fastest most powerful tools for doing so, which means it is also exceptionally powerful and useful for good Active Directory Admins that do their work from the command line. It does the same things that tools like dsquery, LDP, powershell, vbscript/jscript with ADSI can do but it does it so much faster and easier. I have literally had people come to me with things they were doing in PowerShell that took days to run that AdFind could do in hours. There are ways to speed up PowerShell but most of the AD folks out there aren’t good enough to figure out what those are because they are not the most basic way of doing things. I have worked with hundreds of companies and in no case have I run into admins who were more efficient working with AD with PowerShell than people who know what they are doing using AdFind/AdMod. I have had several people over the years say that they would convert me but in the end, with no pushing from me, they convert to using AdFind/AdMod. And let’s face it, if PowerShell was so good, the Hacker Collectives wouldn’t be using AdFind. But to be perfectly clear, AdFind is not a threat to any Active Directory, it is ENTIRELY READ ONLY. The danger is that it can be used to query AD quickly and efficiently and possibly arm someone with data about your environment. The worst rating it should ever have is PUP (Possibly Unwanted Program) or PUA (Possibly Unwanted Application) or LOLBIN (Live Off the Land BINary). The End Point people should be more scared of PowerShell Scripts than AdFind and if they want to get picky about AdFind they should be looking at the actual queries, not that it is being run at all. The Hacker Collectives are using specific queries that are very widely casted nets that normally aren’t needed unless someone is specifically scanning the Active Directory.
There have additionally been some questions on whether or not AdFind is still being developed. It is, in fact I just fixed a bug earlier today. Release times are slower because I work a lot in my real job and I have also been trying to do more non-computer things in my off time but part of the process of keeping my sanity is writing code and I still do a lot with AD at work so I will keep updating AdFind/AdMod until that changes.
//* V01.59.00 2022.0605 o 06/05 Fixed -nirs* sort ordering *
//* Added hacked -[q]list for -nirs for *
//* listing attributes only *
//* BUGFIX: -gco port change message *
//* BUGFIX: Error usage for metafilterattr*
//* o 06/06 Added GT IPA handling (Z vs .0Z) *
//* Added LOCALGTIPA for binenc *
//* Added CURRENTGTIPA for binenc *
//* o 07/11 Updated expiration and header *
//* o 07/12 Added regex to _OBJECT_OWNER *
//* o 08/05 Added -vmeta+ alias for -vmetaplus *
//* o 08/07 Added check for preceding space on att*
//* Added check for admod params *
//* o 08/20 Added -c2 *
//* 2023.0118 o 01/18 Updated expiration and header *
//* o 02/02 Updating usage *
//* o 02/04 Updated some decodes *
//* o 02/21 BUGFIX: / in arbitrary CSV insert fix*
Finally, possibly unexpectedly, I do not intend to fight with the AV/AM/Browser companies on this. I tried this in the past with tools like NETSESS which is another tool that the hackers really liked along with Windows Admins who knew what they were doing. It just isn’t worth my time to fight with the companies as they don’t understand. I have always shared my tools freely to try and help out admins as they can and I know it has saved companies a ton of money and time but it isn’t a money making thing for me and quite frankly to get me to care enough to fight with those companies it would have to be bringing in millions of $$$ a year and then I would hire someone to deal with it.
Finally, dear browser companies. If I want to download something, warn me if you think something isn’t right, but I should be able to easily override your warning without turning off your security measures completely which is quite stupid and makes things even less secure. You don’t own my machines and what I put on them. Firefox and Opera are the only browsers that have properly figured that out.
joe
[1] In my 30 years in the industry there was one AV tools worth using, it was called ThunderBytes and it used intelligent heuristics to determine if apps were doing bad things and didn’t rely on signatures for specific binaries.
![]()