joeware - never stop exploring... :)
Information about joeware mixed with wild and crazy opinions...
5/10/2008
Sheesh… more geek stuff…
This is going to be a “joe sees more movies than usual” summer I think….
http://thedarkknight.warnerbros.com/
5/7/2008
I can’t say I ever thought this would happen…
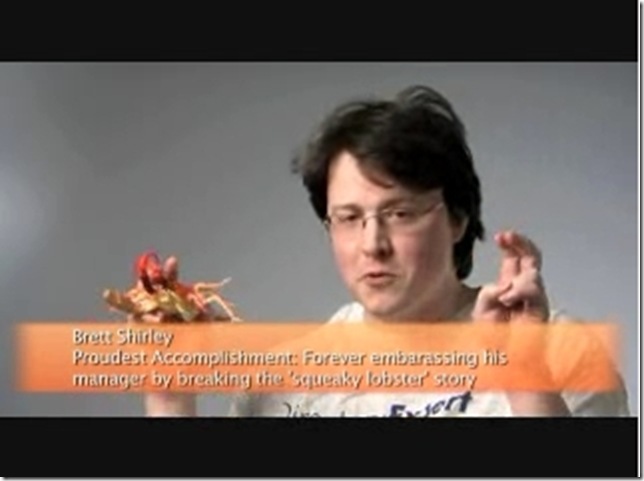
They put Brett out in front of the world…. Oh my[1]…
http://edge.technet.com/Media/Exchange-Server-meet-the-team/
Brett starts at 3:37…. He is awfully video-genic don’t you think? I just want to know why he wasn’t wearing a joeware t-shirt…
Overall, that was a great video and great idea. It shows that the MSFT Dev folks are real people which is something I learned a long time ago and a message I have been trying to spread for just as long. I would love to see this kind of thing out of more teams. There are a lot of brilliant awesome people with great personalities with hilarious stories inside of Microsoft that could be shared.
joe
[1] Don’t get me wrong, I am proud to call Brett a friend. He put the fear of giant bumblebees into me… If you know Brett, ask him about the attack of the giant bumblebee that occurred at the Museum of Flight in Seattle a couple of years back where he nearly killed an MVP – specifically me. If he had killed me via heartattack… everyone would have just said… Ah that’s just Brett…
5/6/2008
Intuition…
Intuition comes very close to clairvoyance; it appears to be the extrasensory perception of reality.
– Alexis Carrel
Possibly good news…
http://news.bbc.co.uk/1/hi/health/7380064.stm
Long-term use of ibuprofen may reduce the risk of developing Alzheimer’s disease, a large US study reports.
Data from almost 250,000 veterans showed those who used the painkiller for more than five years were more than 40% less likely to develop Alzheimer’s.
The study in Neurology reported that some other similar painkillers may also have a protective effect.
Dementia experts said the results were interesting but warned against people taking ibuprofen to reduce their risk.
It is not the first time an association between non-steroidal anti-inflammatory drugs (NSAIDs), such as ibuprofen, and Alzheimer’s disease has been reported but results have been conflicting.
<snip>
I have been using Ibuprofen for a long long time. I am a headache sufferer, pressure fronts rock my world. But maybe it was all to help me stave off Alzheimer’s…
Could be good… Could be bad… Who are we to judge?
Perception makes it so…
There is nothing either good or bad but thinking makes it so.
– William Shakespeare
5/4/2008
Latest version of iTunes (7.6.2)…
…appears to be a processor pig… watch out.
Just did the Apple Update of QuickTime, iTunes, and Safari two days ago and was running iTunes the last couple of days and it kept hanging one of my “fast” machines up. 90% processor and better. Especially on video mode.
5/3/2008
Post Correction… Alternate working title… Who says a single space isn’t important???
In one of my old posts (September 2005) I had some vbscript code to convert an octet string GUID to a friendly GUID string. Well I recently received an email from fellow MVP Michael Smith letting me know he found a bug and a new function that was corrected.
First thought in my mind was… NFW. I am exceedingly careful about things I post, especially code/scripts. But I knew that I had a good function because I used it all over the place and it always aligned with AdFind output…
So I copied from the blog entry and mine and his function into a script and fired in an octet string GUID and sure enough, my function screwed up and his worked…
So I went to one of my scripts that used this function heavily and was used Active Directory Third Edition for decoding Security Descriptors because by darn, if my function was broken that meant that was wrong in the book too which would REALLY SUCK.
I ran the sdlist.vbs script and it worked perfectly fine… So I look again at my function in the test script and I look at the function in sdlist.vbs and they looked the same for all of the logic… wtf…
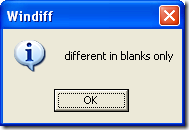
I copy both functions into separate text files and run windiff against them and get
And think well shoot, so my spacing is off… I see that all the time when doing compares like that… So who cares that isn’t going to hurt the script so I go over the logic in the script line by line and the logic is identical…. <BLINK>IDENTICAL</BLINK>.
I start getting very frustrated because I figure I am not seeing something obvious because of a massive headache I have been fighting off all day…
On the third pass through the script I notice one small thing… the function I posted previously had this line
str = “”
the function in sdlist.vbs had this line
str = ” “
Do you see it??? One bloody space character…. ASCII 32/0x20…. $^%$#^&*(@%$#
What difference does that single space make?
G:\Temp>guidc1
Microsoft (R) Windows Script Host Version 5.6
Copyright (C) Microsoft Corporation 1996-2001. All rights reserved.
Object DN : OU=Users,OU=My,DC=test,DC=loc
String GUID : ba1ee8b7248b34408c34841740211a81
BLOG POST Func: {728BEEA1-B348-0844-C348-41740211A81}
Michael Func : {B7E81EBA-8B24-4034-8C34-841740211A81}
sdlist Func : {B7E81EBA-8B24-4034-8C34-841740211A81}
and here is the actual answer
G:\Temp>adfind -b OU=Users,OU=My,DC=test,DC=loc objectguid -s base
AdFind V01.37.00cpp Joe Richards (joe@joeware.net) June 2007
Using server: TEST-DC1.test.loc:389
Directory: Windows Server 2003
dn:OU=Users,OU=My,DC=test,DC=loc
>objectGUID: {B7E81EBA-8B24-4034-8C34-841740211A81}
1 Objects returned
So here is the updated and correct script, this time copied and pasted straight out of sdlist.vbs which is on page 649 of Active Directory Third Edition.
‘****************************************************************************
‘Convert a binary GUID to a string GUID
‘ Convert GUID octet string to Hex characters then arrange in proper order
‘ and add brackets {}
‘****************************************************************************
Function GuidToStr(Guid)
Dim i, str
str = ” “
For i = 1 To Lenb(Guid)
str = str & Right(“0” & Hex(Ascb(Midb(Guid, i, 1))), 2)
Next
GuidToStr = “{“
For i = 1 to 4
GuidToStr = GuidToStr & Mid(str,10-(i*2),2)
Next
GuidToStr = GuidToStr & “-“
For i = 1 to 2
GuidToStr = GuidToStr & Mid(str,14-(i*2),2)
Next
GuidToStr = GuidToStr & “-“
For i = 1 to 2
GuidToStr = GuidToStr & Mid(str,18-(i*2),2)
Next
GuidToStr = GuidToStr & “-“
For i = 1 to 2
GuidToStr = GuidToStr & Mid(str,16+(i*2),2)
Next
GuidToStr = GuidToStr & “-“
For i = 1 to 6
GuidToStr = GuidToStr & Mid(str,20+(i*2),2)
Next
GuidToStr = GuidToStr & “}”
End Function
For completeness and since he went through the trouble of figuring it out and sending it to me… here is Michael’s version as well. You will note he solved it by changing the start points of the MID function in each line. Both solutions work equally well. I would say I probably prefer his version. Less chance for mistake obviously. 🙂
‘****************************************************************************
‘Convert a binary GUID to a string GUID
‘ Convert GUID octet string to Hex characters then arrange in proper order
‘ and add brackets {}
‘****************************************************************************
Function GuidToStr(Guid)
Dim i, str
str = “”
For i = 1 To Lenb(Guid)
str = str & Right(“0” & Hex(Ascb(Midb(Guid, i, 1))), 2)
Next
GuidToStr = “{“
For i = 1 to 4
GuidToStr = GuidToStr & Mid(str,9-(i*2),2)
Next
GuidToStr = GuidToStr & “-“
For i = 1 to 2
GuidToStr = GuidToStr & Mid(str,13-(i*2),2)
Next
GuidToStr = GuidToStr & “-“
For i = 1 to 2
GuidToStr = GuidToStr & Mid(str,17-(i*2),2)
Next
GuidToStr = GuidToStr & “-“
For i = 1 to 2
GuidToStr = GuidToStr & Mid(str,15+(i*2),2)
Next
GuidToStr = GuidToStr & “-“
For i = 1 to 6
GuidToStr = GuidToStr & Mid(str,19+(i*2),2)
Next
GuidToStr = GuidToStr & “}”
End Function
joe
AdFind Shortcuts for Base DN
In my previous article on DN formats (http://blog.joeware.net/2008/05/03/1226/) I talked about the various Base DN shortcut formats available and hinted that AdFind has some shortcuts of its own. To me these are all, well they aren’t even second nature because I use them almost exclusively. I am bringing it up because even people who use AdFind a lot have watched me or my friends use AdFind and see them and say “Wow I had no idea… AdFind is cool.” Indeed. 🙂
The idea behind the shortcut bases was to be able to write generic scripts where I didn’t have to first work out the DNs so submit the AdFind queries. This way I can tell someone, well I need to see what your uPNSuffixes attribute looks like, run this command
adfind -partitions -s base upnsuffixes
and it will work in every forest period. I know there are consultants and support professionals everywhere that love me for that one… It can literally save a 5 minute conversation on how to find that spot in the directory.
So here are the shortcuts currently in the publicly available version of AdFind (V01.37.00) from the usage screen (adfind /??)
-null Use null base.
-root Determine and use root partition for BaseDN.
-config Determine and use configuration partition for BaseDN.
-schema Determine and use schema partition for BaseDN.
-default Determine and use default partition for BaseDN.
-rb xx Relative Base, use with special BaseDN’s above.
So you could specify -default and -rb cn=users.
-forestdns Use ForestDNS NDNC for base.
-domaindns Use DomainDNS NDNC for base.
-dcs Use Domain Controllers container of default domain for base.
-gpo Use System Policies container of default domain for base.
-psocontainer Use PSO Container of default domain for base.
-ldappolicy Use Ldap Query Policies container for base.
-xrights Use Extended Rights container for base.
-partitions Use Partitions container for base.
-sites Use Sites container for base.
-subnets Use Subnets container for base.
-exch Use Exchange Services container for base.
-fsps Use Foreign Security Principals container for base.
Quick descriptions
-null : Null base or Base = “”
-root : DN to the root domain of the forest
-config : DN to the configuration container of the forest
– schema : DN to the schema container of the forest
-default : DN to the default domain for the DC contacted. For ADAM this will select the first App Partition unless a default app partition is defined in ADAM (see msDS-defaultNamingContext).
-rb xx : Now this is a cool little feature that lets you specify a special shortcut base but then prepend some more onto the DN that is used for that. So for example say I want the domain controllers OU of the default domain I would specify -default -rb “OU=Domain Controllers” and AdFind will determine the default domain DN and then prepend “OU=Domain Controllers,” to is to you get the whole DN to the Domain Controllers OU.
-forestdns : DN to the ForestDNS Application Partition
-domaindns : DN to the DomainDNS Application Partition
-dcs : DN to the Domain Controllers OU – so you don’t have to type that long -default -rb “OU=Domain Controllers” mentioned above. 😉
-gpo : DN to the System Policies Container
-psocontainer : DN to the Password Settings Object Container (Windows Server 2008 obviously…)
-ldappolicy : DN to the LDAP Query Policies container in the configuration partition
-xrights : DN to the Extended Rights container in the configuration partition
-partitions : DN to the partitions container in the configuration partition
-sites : DN to the sites container in the configuration partition
-subnets : DN to the subnets container in the configuration partition
-exch : DN to the Exchange container in the configuration partition
-fsps : DN for the Foreign Security Principals container
There is also a special shortcut base I have that doesn’t fit exactly in with the above, that is -gcb. That is the combination of the -gc and -null switches so it sets you up to search the GC at the base of the forest.
Cool right?
[joeware – never stop exploring… :) is proudly powered by WordPress.]